
SQL Injection Using UNION. SELECT name, description, price FROM products WHERE category= AND 1=UNION SELECT username, passwor FROM members. In this tutorial we will learn how to inject Union based injection.
In our last tutorial we learnt how to find out the number of columns used under the query so that we can use Union select statement. The result of the forged query will be joined to the result of the original query, allowing the tester to obtain the values of columns of other tables. This cheat sheet is of good reference to both seasoned penetration tester and also those who are. How do you use Union in SQL? The UNION operator is used to combine the result-set of two or more SELECT statements.
Why do you want to re-invent the wheel? It allows the attacker to combine the of two or more SELECT statements into a single result. Look at the following example which creates a SELECT statement by adding a variable (txtUserId) to a select string. The only difference between numeric parameters and string parameters is that the latter is enclosed between quotes.

The application is said to be vulnerable to In-band when the communication between the attacker and the application happens through a single channel. In this technique, the user combines the query and get the result back as some part HTTP response. The reason I ask is because I am trying to write my own sql injection tool but do not know the best way to determine the exploitable columns using the UNION SELECT method (having already found out the number of columns using ORDER BY).
UNION , any arbitrary result can be SELECTe. Notes (FYI): UNION is used to combine the result from multiple SELECT statements into a single result set. That control a web application’s database server.
Now remember – y’all play nice with the bits and pieces you’re about to rea ok? There are total courses. But for UNION operator there Union Based Sql Injection. Note that you need to enumerate the number of columns first, this can be achieved by using the ORDER BY function or using UNION with NULL values.
In this series, I’ve endevoured to tabulate the data to make it easier to read and to use the same table for for each database backend. Check for UNION function With union we can select more data in one sql statement. Then, it provides a single result, which can provide crucial data about the system.
This type of attack uses the UNION statement, which is the integration of two select statements, to obtain data from the database. This gap occurs when the input from the user is not filtered correctly, for example. It is a top threat for a few reasons.
These malicious injections have been regularly starring in the OWASP Top-lists for years and they took the first place in. With nobodyhavethisusername we make sure this query will not return based on left of the union select. Union select can only return columns (I guess) and app uses i username, password columns so we returned this columns with UNION SELECT. Unless you have the source code of the application, you will have to guess this number. Mitigating this attack vector is both easy and vital for keeping your information safe.
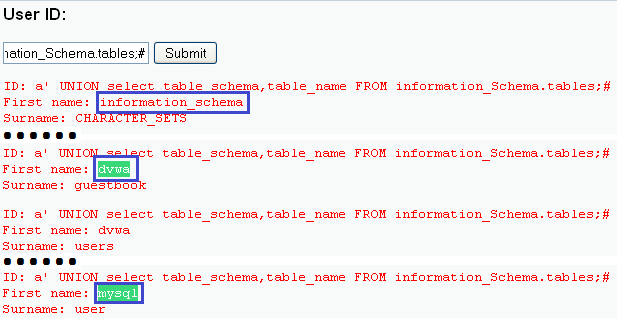
It generally allows an attacker to view data that they are not normally able to retrieve. Build A union Based Query and then Get Data from the database. These attacks only work with apps that internally use SQL. An injection attack allows an attacker to alter the logic of the query and the attack can lead to confidential data theft, website defacement, malware propagation and. If flaws are detecte our online tool offers detailed information about the risks you are exposed to and recommendations on how to perform an effective remediation process.
This information may include any number of items, including sensitive company data, user lists or private customer details. Most attackers are just into using the union statements, information_schema and order by statements and neglecting some of the techniques just for the sake of getting the username and the password of the website administrator. The infamy of this attack has even made its way into the popular XKCD comic. The key to avoiding these vulnerabilities is to sanitize and escape anything you send to the database.
In WordPress the easiest way to do this is by using the prepare() method and using placeholders in your SQL.
Geen opmerkingen:
Een reactie posten
Opmerking: Alleen leden van deze blog kunnen een reactie posten.